Publishing the WorkZone Mobile iOS app on Microsoft Intune (Azure Portal)
Prerequisite:
- Internal domain users are synced to Azure Active Directory and user groups with access to WorkZone Mobile exist.
- Conditional access policies are created. See Set up security and access from mobile devices.
- Intune is set up so that mobile devices are managed and the devices are marked as "in compliance" by Intune.
Log in to the Microsoft Azure portal.
Add the Microsoft Authenticator app
Publish the Microsoft Authenticator app to make it available on the Company Portal. Users can then easily download it and use to log in to WorkZone.
- Go to Microsoft Intune.
- Click Client apps > Apps.
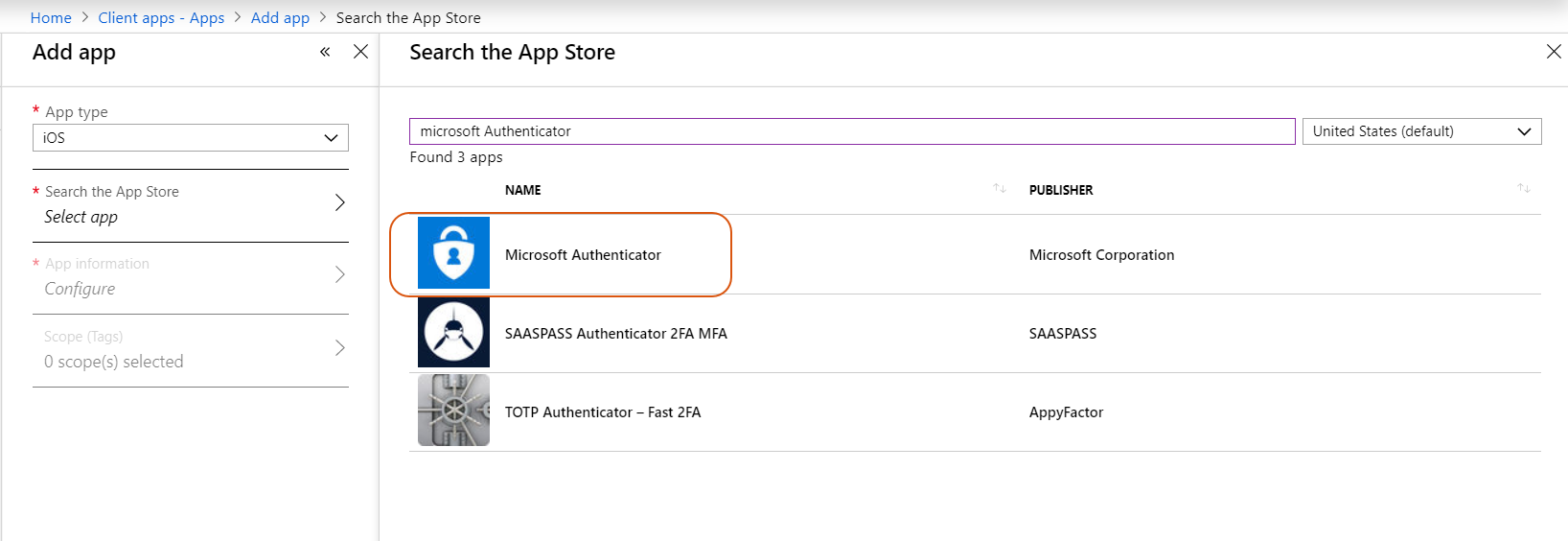
- Click Add. In the App type field, select Store app > iOS.
- Click Search the App Store.
- Enter Microsoft Authenticator in the search field and select Microsoft Authenticator among the available options.
- Click Select and then click Add.
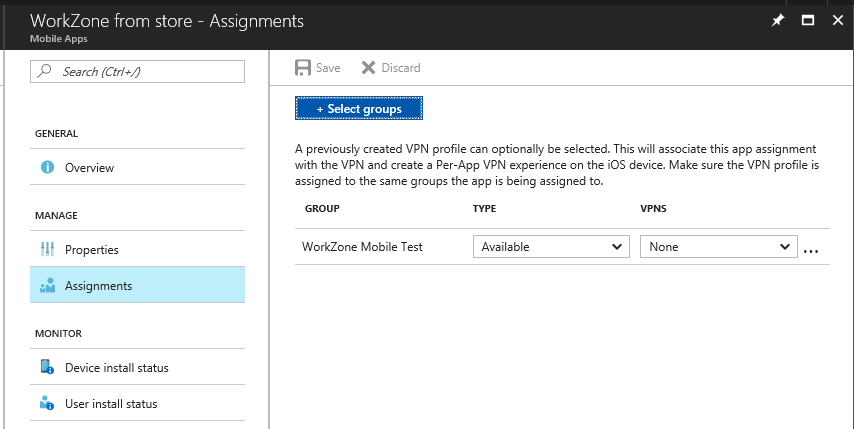
- Click Assignments, and select the Azure Active Directory groups or users who should get WorkZone Mobile in their Company Portal.
- Click Save.
Add the Intune Managed Browser app and the Microsoft Office apps
Optionally, you can add the Intune Managed Browser app and a number of Microsoft Office apps to improve user experience with the WorkZone Mobile application.
- Go to Microsoft Intune.
- Click Client apps > Apps.
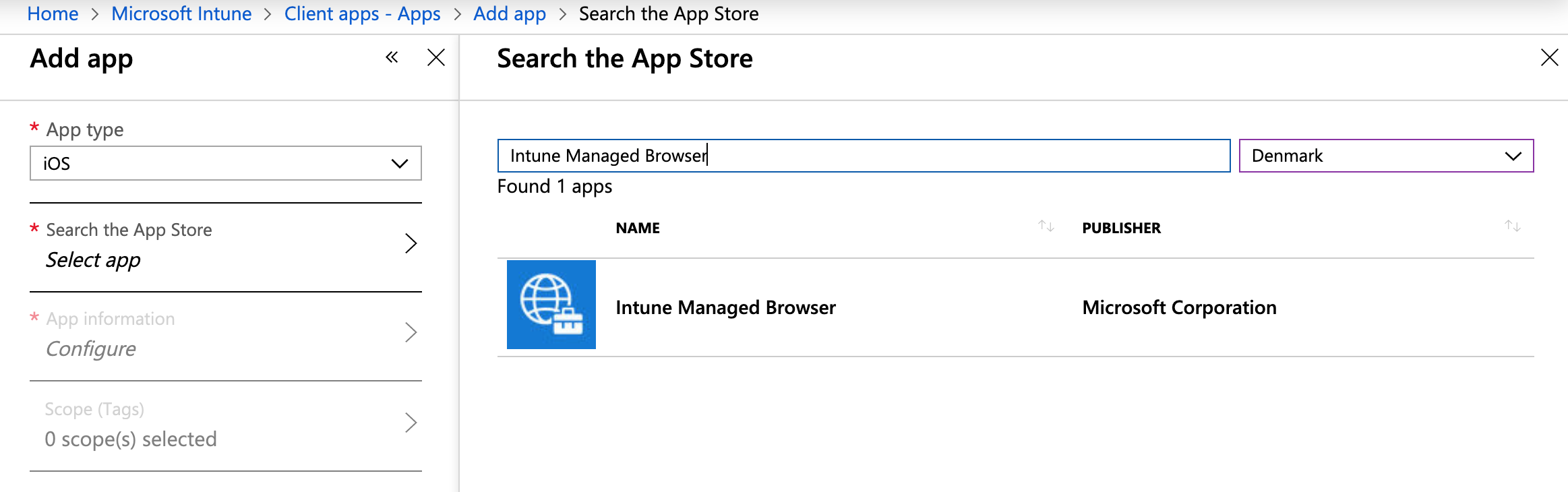
- Click Add. In the App type field, select Store app > iOS.
- Click Search the App Store.
- Enter Intune Managed Browser in the search field and select the application.
- Click Select and then click Add.
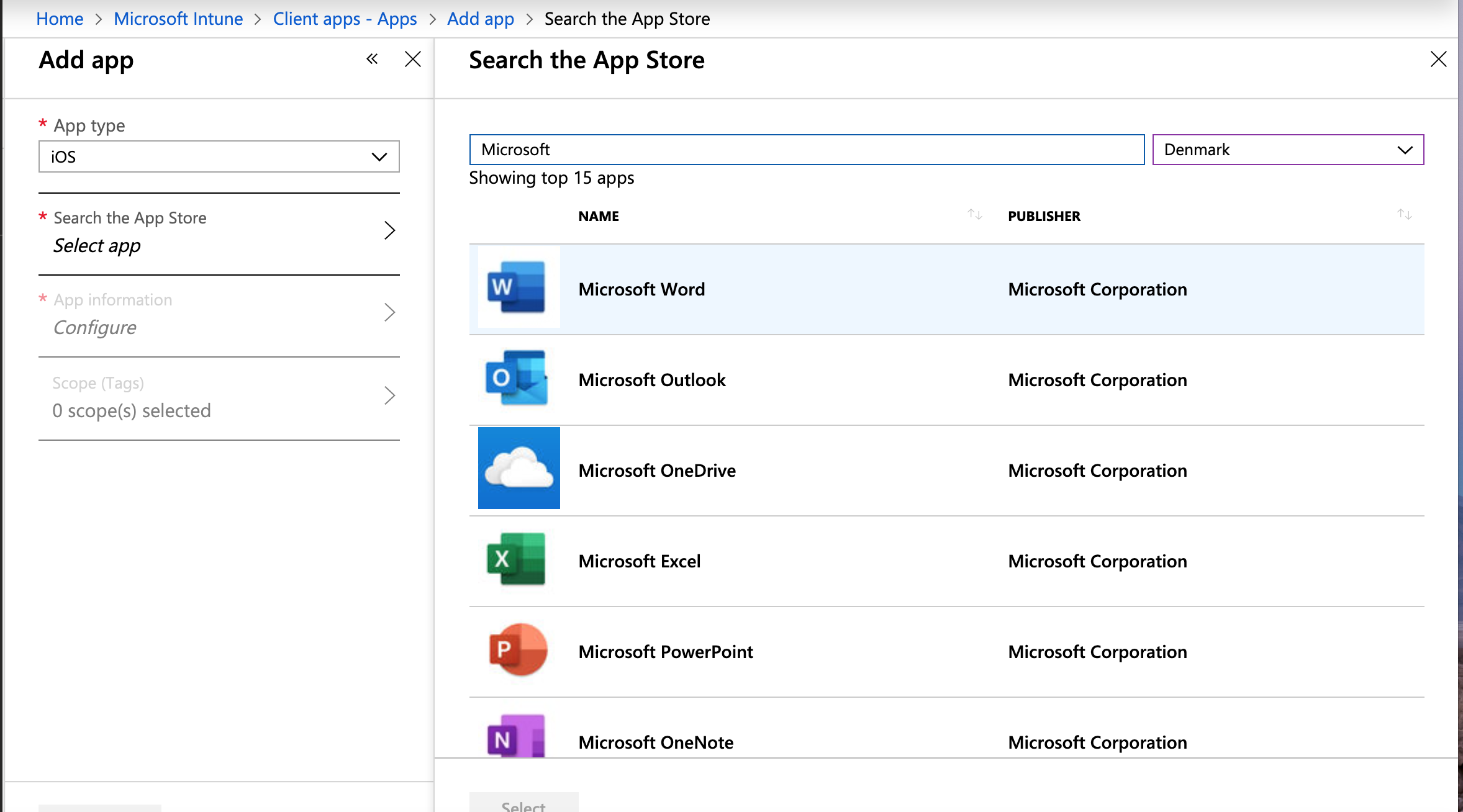
- Enter Microsoft in the search field and select the applications that you want to add.
- Click Select and then click Add.
Add the WorkZone Mobile app
- Go to Microsoft Intune.
- Click Client apps > Apps.
- Click Add. In the App type field, select Store app > iOS.
- Click Search the App Store.
- Select Denmark among countries and type "WorkZone for Intune" in the search field. Search for WorkZone for Intune and select KMD WorkZone for Intune published by KMD A/S, and click OK.
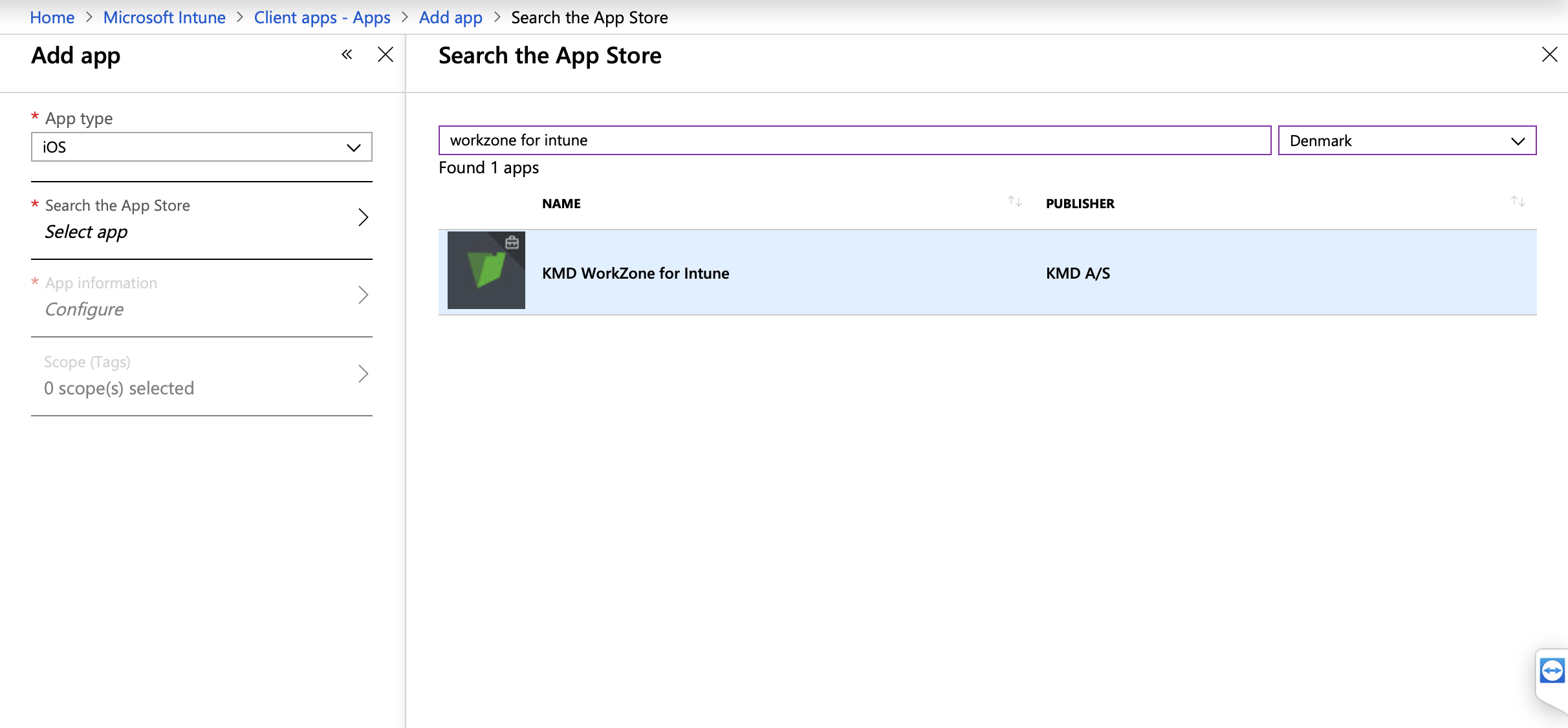
- Click Select and then click Add.
- Click Assignments, and select the Azure Active Directory groups or users who should get WorkZone Mobile in their Company Portal.
- Click Save.

Create an App configuration policy for iOS
WorkZone Mobile supports pushing certain connection settings to the mobile devices through Intune. This is done by creating an app configuration policy and assigning it to the app users.
- Log in to Microsoft Intune.
- Go to Apps > Policy > App configuration policies.
- Create a new policy with the following settings:
- Device enrollment type: Managed devices.
- Name: Enter the name for your app configuration policy.
- Platform: iOS/iPadOS.
- Targeted app: KMD WorkZone Intune - KMD - Managed iOS.
- Configuration settings format: Enter XML data.
- Copy and paste the code below.
-
Replace the
[URL to your WorkZone server],[Redirect URI of the native WorkZone app], and[WorkZone App (Client) ID]with the values from your setup.Tip:
- Copy the exact value of Redirect URI from your app registration in Azure portal, under App registrations > [Name of your WorkZone app] > Manage > Authentication > iOS/ macOS > Redirect URIs.
-
Copy the
[WorkZone App (Client) ID]from your app registration in Azure portal, under App registrations > [Name of your WorkZone app] > Essentials > Application (client) ID.
For example:
<dict>
<key>mamserverurl</key>
<string>https://test.workzone-rd.dk</string>
<key>mamredirecturi</key>
<string>msauth.dk.kmd.workzone.intune://auth</string>
<key>mamclientid</key>
<string>30gftg48-b8bg-238o-6f32-a0g3kj445e81</string>
<key>mamuserprincipalname</key>
<string>{{userprincipalname}}</string>
</dict>
- Save the policy.
- Click Assignments, and assign your newly created policy to a user group, if needed. For example,
MS_Licensed_Users. - Save your changes.
<dict>
<key>mamserverurl</key>
<string>[URL to your WorkZone server]</string>
<key>mamredirecturi</key>
<string>[Redirect URI of the native WorkZone app]</string>
<key>mamclientid</key>
<string>[WorkZone App (Client) ID]</string>
<key>mamuserprincipalname</key>
<string>{{userprincipalname}}</string>
</dict>
