About container-based hosting
KMD WorkZone offers Software as a Service (SaaS) via cloud services and privately hosted deployment models. These models are easy to get started on and provide the expected benefits of a SaaS solution whether you are on a public cloud, EU cloud, or private cloud setup.
Some organizations have strict requirements for compliance or specific location or security related needs, that require the option of privately hosting WorkZone. In these cases, you will either need to host WorkZone in your own data center, through a private cloud subscription, or by using a hosting partner, such as a government data center, that complies with your specific requirements.
WorkZone hosting concepts
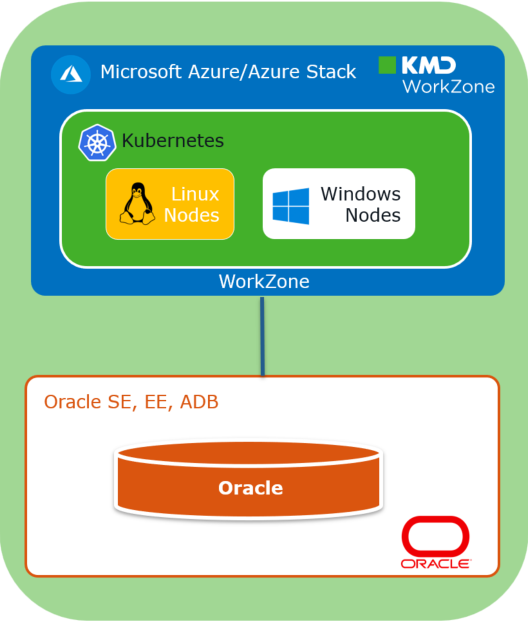
The hosting infrastructure for WorkZone is container-based and is based on standard application and database layers.
Application components
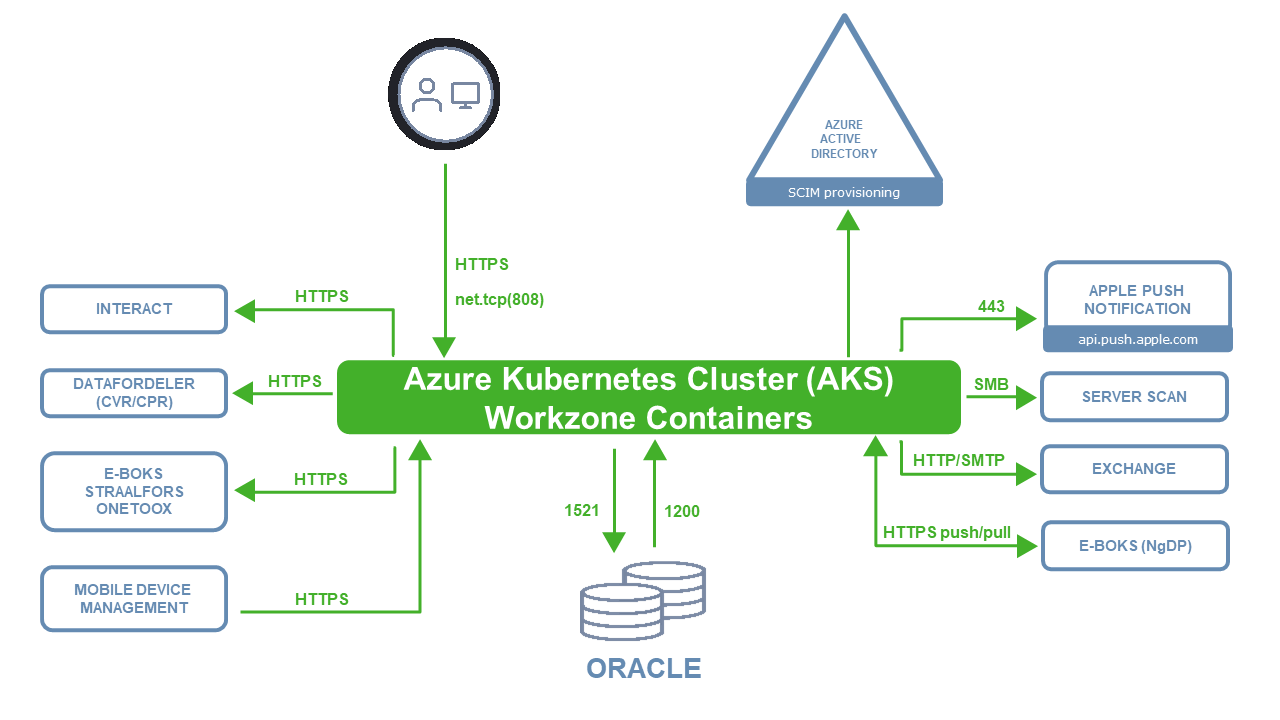
The individual infrastructure elements are described here.
- Application server - The application server is based on a container-based hosting model that is orchestrated via a Kubernetes platform. The Kubernetes platform manages Windows and Linux worker nodes in order to run all the relevant WorkZone containers. Most of the containers are based on Windows where only a few are currently Linux containers. See Kubernetes in the support matrix.
- Database server – The database server is a standard Oracle database that can be hosted in Oracle OCI (Oracle Cloud Infrastructure) as an Autonomous Database Server or hosted on-premises with either Oracle SE (Standard Edition) or Oracle EE (Enterprise Edition). See Oracle platforms.Note: As an Oracle ISV, WorkZone offers on-premises Oracle licenses as part of the WorkZone licenses that use the Oracle AFSU license model.
- Entra ID Integration – The authentication and authorization model for WorkZone is based on Microsoft Entra ID as a provider. The user authentication is based on Entra ID and the authorization is based on Entra ID groups that are synchronized by the Entra ID SCIM protocol. See Enroll WorkZone - Cloud Edition in Azure and set up SCIM provisioning.
- Microsoft Entra ID as a customer directory - For more information, see Register WorkZone in Azure.
- Mail integration - The server side mail integration in WorkZone has two shapes; a standard SMTP integration for notifications and a deeper mail integration for sending Process related messages that are more rich in content, and which is also used for mail monitoring services. The more complex mail integration requires Microsoft Exchange. See Windows Server, Exchange Server, and Oracle.
For more information about the business modules of WorkZone, please refer to WorkZone modules and services.
About Cross-Origin Resource Sharing (CORS)
Cross-Origin Resource Sharing (CORS) is a mechanism that enables web browsers or other web clients to safely request restricted resources from domains outside of the domain that the web page was loaded from.
Often, cross-domain requests are prevented unless the request originates from a requester on the same domain as the service resides (same-origin security policy). This is done to reduce threats from off-site attacks.
CORS defines a way to determine whether requests for services can be authorized by the server when the requests are made from a browser with a web page that is not loaded from the same domain as the server. This authorization allows a across-origin request to be performed or its data to be passed by the browser to the requesting party to be executed by the requesting browser. This combines the freedom and flexibility of accepting all cross-origin requests with the increased security of same-origin requests by defining which sites may successfully send requests and receive access to services.
WorkZone uses CORS to enable web pages to access WorkZone services, such as WorkZone PDF Engine, WorkZone Process, and WorkZone OData when these pages are loaded from different domains.
Configure CORS in WorkZone
If WorkZone services are to be requested from web pages with other origins (for example WorkZone Client and WorkZone Configurator applications are hosted on a different host than the Process service), you must configure the CORS parameters AllowedCorsOrigins and AllowedCorsHeaders for WorkZone PDF Engine, WorkZone Process and WorkZone OData.
See also:
Networking infrastructure
This diagram illustrates the WorkZone infrastructure.
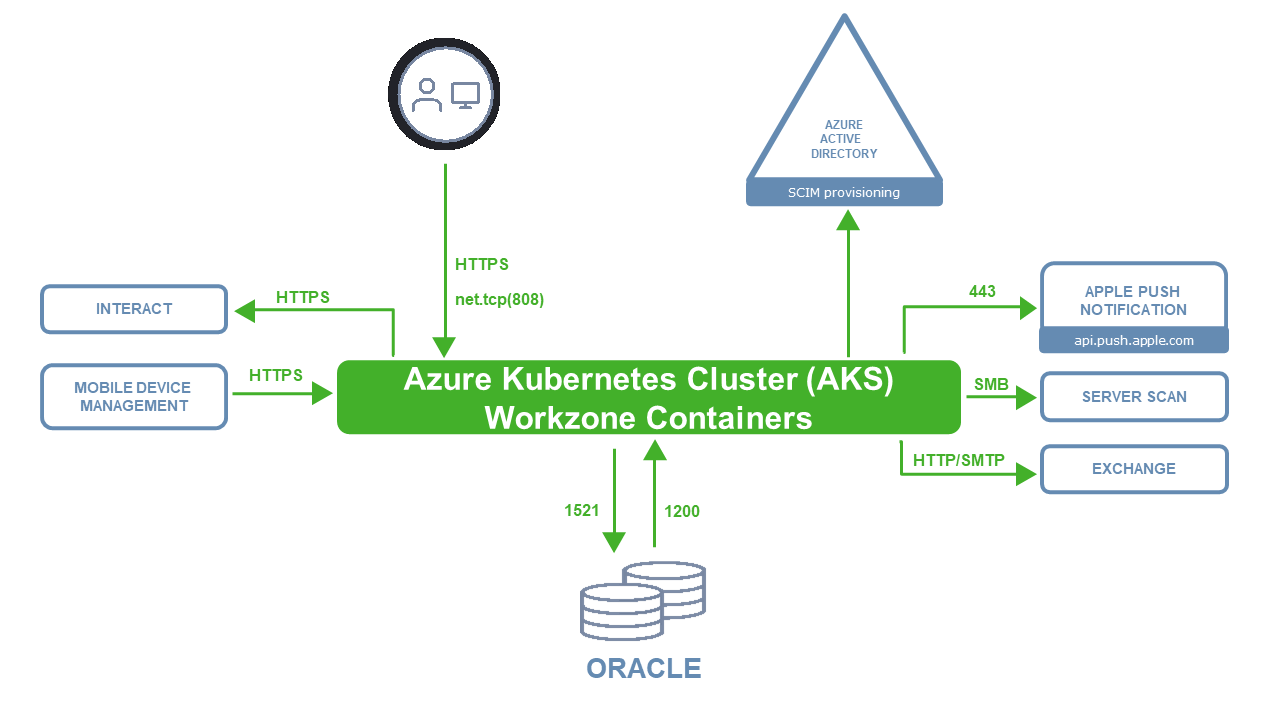
Firewall directions and network ports
The arrows in the diagram above illustrate the firewall direction and the ports indicated must be opened for traffic in order for WorkZone to operate correctly.
Special note regarding TCP port 1200
The network TCP port 1200 (configurable) is required to be open for incoming traffic on the web server in order to receive chat notifications from the Oracle database to the new Notifications web application. If the Windows firewall is enabled on the web server, it will be opened automatically when installing WorkZone Content Server using Olympus.
If the port is not open, the chat feature will not receive notifications regarding changes to chats. If another firewall is configured between Oracle and the web server, the TCP port 1200 (configurable) must be opened there as well.
net.tcp(808)
net.tcp(808) is only used by WorkZone for Office.
Network connections
| Component | Local Ports | Connects to | Protocol | Notes |
|---|---|---|---|---|
|
AD replicator |
N/A |
Oracle, DC |
N/A |
Connected to Oracle when the replication is active. Time depends on the size of the Active Directory. |
|
OCR and FIX agent |
N/A |
Oracle |
N/A |
Always connected to the Oracle while the NT Service is running. |
|
SUB/WFM agent |
N/A |
Oracle, SMTP |
N/A |
Always connected to the Oracle while the NT Service is running. |
|
Service Channels |
N/A |
Oracle, File, POP3 |
N/A |
Always connected to the Oracle while the NT Service is running. |
|
Scan Station |
N/A |
File server or FTP |
WorkZone Certificates
| Product/Module | Certificate | Certificate name/type | Usage | For more information |
|---|---|---|---|---|
|
WorkZone Process/SmartPost |
Digital Post Remote print |
Functional certificate (funktionscertifikat) |
Send and receive SmartPost messages. |
|
|
WorkZone Process/Interact |
Interact |
Functional certificate (funktionscertifikat) |
Load data from Interact forms in to WorkZone |
|
|
WorkZone Process |
Push notification certificates |
Apple Push Services: dk.kmd.WorkZone Apple Push Services: dk.kmd.workzone.intune |
Send notifications from WorkZone Process to WorkZone Mobile The certificates are installed in the certificate store as part of the WorkZone Process installation. |
Configure push notification certificates for WorkZone Mobile |
|
CVR Integration |
FOCES certificate |
Functional certificate (funktionscertifikat) |
Integration with Det Centrale Virksomhedsregister (CVR) in Denmark. |
|
|
WorkZone |
SSL Certificate |
SSL Certificate |
SSL (Secure Sockets Layer) Certificates must be configured in the Internet Information Server (IIS) as defined by Microsoft. |
See the Microsoft articles: |
Important: Running the WorkZone Process modules requires that your certificates are valid. During installation, you can choose to disregard certificate errors and thus allow running the modules in environments with invalid certificates. Note, however, that this is not a recommended option. In general it should only be possible to run WorkZone Process in environments with valid server certificates.
Kubernetes and WorkZone
These are the current and expected future Kubernetes options for hosting WorkZone. Please reach out to KMD WorkZone, if you have questions on the future platform support.